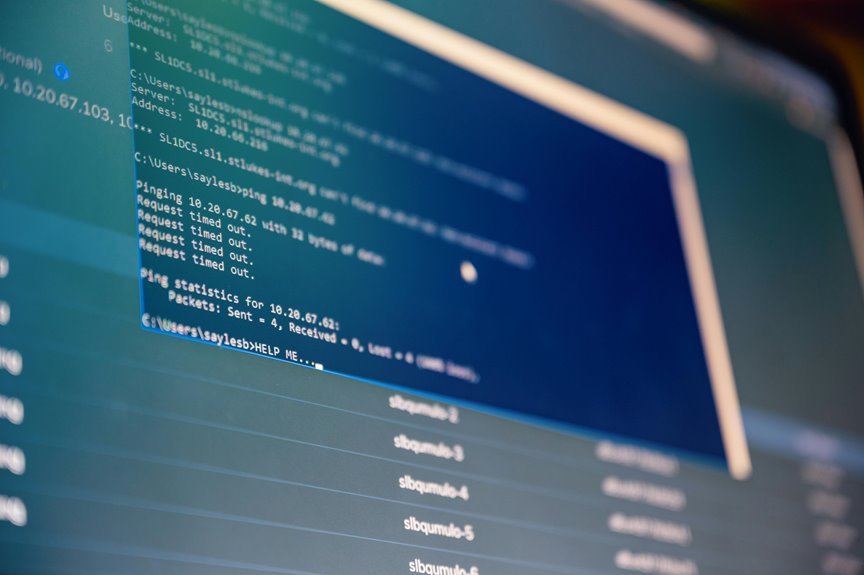
The IP address 12.16.198.1100 serves as a critical identifier in network environments. Its role in system traffic analysis enables administrators to monitor data flows effectively. By employing techniques like packet capture and anomaly detection, organizations can pinpoint irregularities and enhance security. Various tools further aid in real-time traffic monitoring, offering insights into user interactions. Understanding these components is essential for optimizing network performance and resource management. What challenges arise in this complex landscape?
Understanding IP Addresses and Their Significance
Although the intricacies of network communication can be complex, understanding IP addresses is fundamental to system traffic analysis.
An IP address serves as a unique network identification tool, enabling the tracking of data routing processes. By analyzing these addresses, one can uncover traffic patterns that reveal user behaviors and network interactions, ultimately facilitating more effective management and optimization of network resources.
Techniques for Analyzing System Traffic
Analyzing system traffic requires the implementation of various techniques that enable the examination and interpretation of data flows within a network.
Key methods include packet capture, which facilitates the collection of data packets traversing the network, and anomaly detection, which identifies deviations from normal traffic patterns.
These techniques enhance network security and performance, allowing for timely responses to potential threats or inefficiencies.
Tools for Effective Traffic Monitoring and Analysis
Effective traffic monitoring and analysis rely on a variety of specialized tools designed to capture, inspect, and interpret network data.
These tools facilitate real-time monitoring, enabling network administrators to detect anomalies swiftly.
Additionally, traffic visualization applications provide intuitive graphical representations, aiding in the identification of patterns and trends.
Together, these technologies empower users to maintain optimal network performance and enhance security measures.
Conclusion
In conclusion, the significance of effective system traffic analysis cannot be overstated, particularly in an era where cyber threats are increasingly sophisticated. Notably, studies indicate that over 80% of network breaches exploit known vulnerabilities, underscoring the necessity for robust monitoring tools. By leveraging techniques such as packet capture and anomaly detection, network administrators can not only enhance security but also optimize network performance, ensuring that resources are allocated efficiently in response to real-time traffic insights.